Fat tyre bike - Is it worth buying it?
Buying an electric bike with fat tyres is absolutely worth it, especially if you plan to ride on dirt trails, and give yourself a cool look! They don't necessarily cost more than other electric bikes and the ride comfort they offer is unbeatable, people will turn around in the street looking at you.
Perfect in the city
Although fat bikes are often referred to as winter mountain bikes, they are also a perfect bike in the city
Maximum control
It is particularly easy to control, the large support surface on the ground guarantees extreme stability even on the most uneven terrain
They are light
The extreme section of the tires ensures a shock-absorbing effect that thus saves on the weight of front and rear suspensions
The Best Electric Fat Bikes of 2024
The best electric fat bikes of 2024 In this article, you will find a quick guide to choosing the electric fat bike that best suits your needs, with recommendations for the models with the best value for money for adults. There are fat bikes of different qualities and it is often difficult to choose if the basic concepts such as power, range, transmission or braking system, among others, are not clear.
Lankeleisi
Powerful 1000W electric motor allows the electric bicycle to reach a maximum speed of 33-40kmh and has a climbing ability of 35°
Engwe
Amazing 750W Electric Fat Bike 12.8Ah 48.1V Battery regenerative braking, hydraulic brakes. Maximum speed of 40kmh
ADO A20F
Equipped with an aluminum alloy frame, 500 Watt brushless motor, magnesium alloy rims, 7-speed Shimano gearbox, IPX5 waterproof
Sondors X
The Storm is a minimal fat bike project without a lot of technological research, in order to offer an electric pedal assisted bike with fat wheels at an affordable price
Aventon Aventure
The Aventon Aventure e-bike is explorer and commuter in equal parts, with features and accessories to take any type of cyclist almost anywhere they need (or want) to go
Cyrusher XF800
With a range of 80 km and its massive 26-inch wheels, it allows you to tackle rough terrain such as snow, beaches and mountains without any difficulty
Where to Buy Fat Tire Electric Bikes?
In this shop they are available in almost all versions: such as city bikes, folding bikes, mountain bikes or trekking bikes. They are absolutely trendy and are among the most popular sports equipment today.
Our selection of the 5 best fat tire bikes
Do you want to know more about fat bike electric bikes and want to know which are the most sold and recommended in 2024? We can help you. In this historical moment when looking for fat bike electric bike you can easily find several very different electric bike models.
1 - ADO A20F Best of all
Battery range: 80 km
The time has come for you to take a real leap in quality by choosing a highly innovative, technological and cutting-edge option. By choosing ADO A20F, you will have all this and much more. In our opinion, it is the best folding electric bike you can find in 2024. Its performance is truly unbeatable!
Its exceptional range of 80 km will give you all the energy you need to travel long distances, both in the city and in the countryside. With this e-bike you can go outside and enjoy a beautiful sunny day, pedaling without ever stopping but at the same time without tiring. The engine is very powerful and has a gearbox that allows you to adjust the speed in 7 different levels. Because of all these characteristics, the reviews of the buyers are all favorable.
Why buy the product?
- 36V 500W motor: the pedal assistance that the motor offers you to reach speeds of up to 35 km/h. You will be able to get where you want in a practical and fast way.
- SAMSUNG battery: worried about the autonomy of ADO A20F? You don't have to be, really! The SAMSUNG 36v battery will provide you with enough energy to travel up to 80 km continuously before you have to worry about recharging it again. In addition, it can be conveniently charged via USB cable.
- SHIMANO Shift: Make gear changes very quickly and precisely. The SHIMANO integrated gearshift of this folding electric bike will allow you to select up to 7 different options. This advantage is very useful when you are on difficult routes such as in the case of steep climbs.
- KENDA Tyres: Thanks to the 20-inch KENDA tyres of this electric bike, you will have the freedom to move around the city quickly and agile, regardless of the traffic. And of course, safety is also guaranteed, they offer the vehicle exceptional stability.
- Adjustable Front Suspension: The adjustable front suspension is perfect for occasions when you ride your bike on uneven ground, such as on dirt roads. Your driving experience has never been so enjoyable!
- LED display: its LED display will help you to have total control of the device as it allows you to turn on the battery, manage the lights and many other interesting functions. There is no doubt, if you were looking for the best folding electric bike today, you have it right under your eyes.
- Adjustable handlebar: enjoy maximum comfort while driving! The handlebar of this folding bike is made of sturdy aluminum, but is still comfortable. It is fully height adjustable, so you won't have any problems regardless of your height.
- Fully foldable: take it wherever you want! Your ADO A20F electric bike is completely foldable, which makes it very compact. It proves excellent to be transported also by car or public transport. Finally, you will notice that it is also much lighter than many other models that you can find on the market today.
2 - Lankeleisi XF4000 a Power Monster - Maximum speed 50km/h
The LANKELEISI XF4000 has large capacity removable battery equipped with 48V 16Ah lithium battery, which is made of high-performance Panasonic 18650 battery cells offering up to 30-50km on pure electric and up to 60-80km with pedal assist mode.
The powerful brushless 1000W motor makes it significant performance on slopes up to 35°.
Why buy the product?
- 3 OPERATING MODES Pedal assist mode: the motor will assist you with a moderate amount of power as you pedal on the bike.
- HIGH SPECIFICATION CONFIGURATION: 6061 aluminum alloy softail frame, perfect advanced welding technology, pipe wall thickness up to 1.6mm, adopts contemporary advanced painting process.
- RIDING MODES: Ride the bike normally as you would any other bike.
- Frame Warranty: 2 years; Controller, charger and battery: 6 months; Other electrical parts: 3 months.
- BETTER EXPERIENCE Intelligent 5-level pedal assist systems, the perfect combination of pedaling and power assistance.
- LCD Display: Equipped with a large 3.5” LCD display with intelligent multifunction button.
- Fully electric mode: rotate the accelerator to any desired increase in power to power the bike's engine.
- Assembly: The bike finished assembling 90% before shipping, usually you need to assemble the saddle, pedals, handlebar and front wheel.
- LARGE CAPACITY BATTERY: Equipped with 48V aluminum alloy external lithium battery, made with high performance high quality 18650 battery cells, higher energy density and longer use time, with lithium battery protection plate.
- BRAKES: Top brand speed control system and Power-Off hydraulic disc brake system.
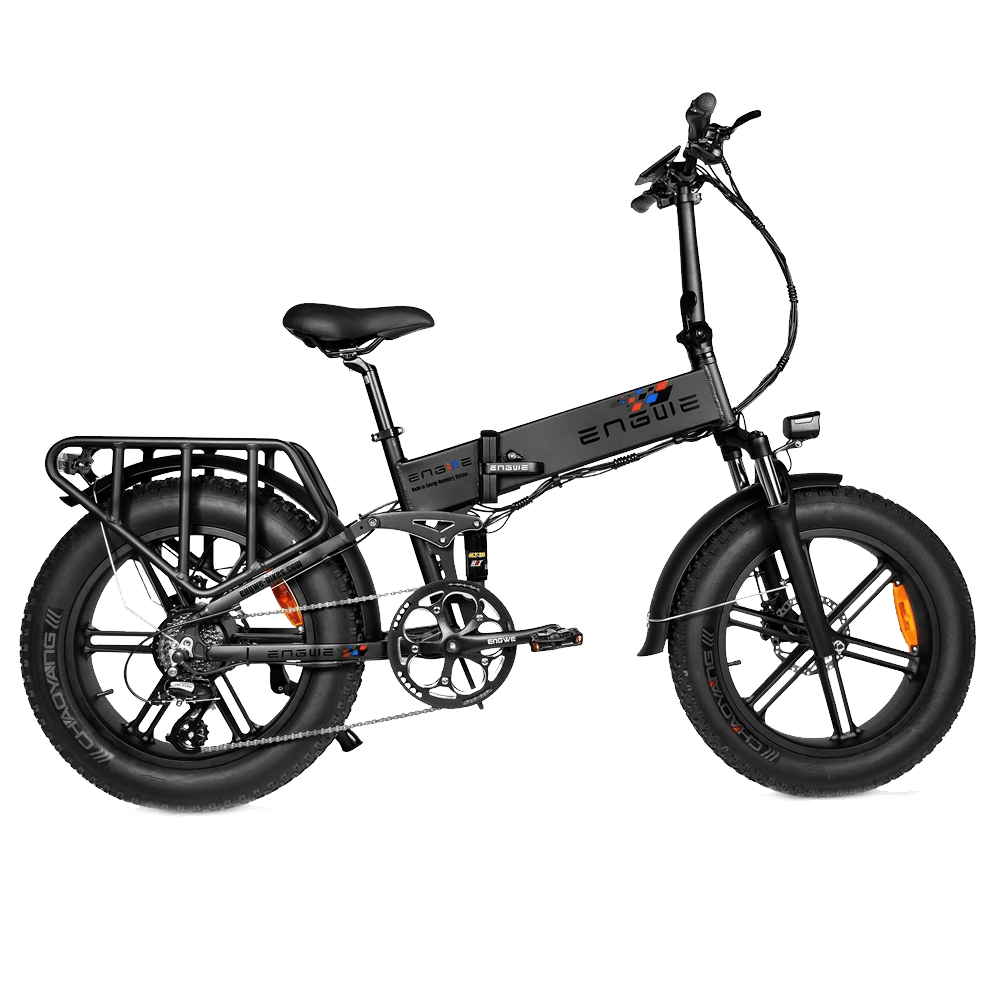
3 - ENGWE ENGINE PRO 750W - Folding Fat Tyre E-bike
On the EP-2 Pro, we have a powerful 750W motor, which is combined with reinforced 20" wheels, as well as a very large battery and many pedaling functions with various levels of speed. In addition to this we have a convenient LCD display from which to monitor all our driving activity.
It has a significant plus that resides in charging on the go thanks to the I-ERS Power Regeneration system. In addition, the integrated display is now in color and much more complete and we have an 8-speed Shimano gearbox. Finally, there are double hydraulic brakes.
Why buy the product?
- 20 inch FAT Tyres Wider, larger diameter and shock absorbing tyres that make driving more comfortable.
- 3 Driving modes: you can choose the driving mode between: Electric, normal or pedal assist.
- High Capacity Battery: It has a 12.8 Ah, 48v high capacity lithium battery, which allows for greater range and speed.
- Support App control: Thanks to this function you can have everything under control, firmware that can always be updated.
- BETTER EXPERIENCE Intelligent 5-level pedal assist systems, the perfect combination of pedaling and power assistance.
- LCD Display: Equipped with a large 3.5” LCD display with intelligent multifunction button.
- Super powerful Brushless motor: Latest generation 750W motor, speeds up to 45 km/h and range up to 60 km.
- Built-in USB Port: Power other mobile devices with a built-in USB port.
- Frame: This folding electric bike is made of lightweight yet strong aluminum with anti-rust and anti-exposure coating.
4 - ENGWE EP-2 750W - Folding Electric Mountain Bike
ENGWE is a Shenzhen-based company founded in 2014 that designs high-quality, stylish and durable electric bicycles that perform excellently in a multitude of different environments. Their slogan is "What we want is to give you a new way to have fun while driving". Let's see all the details of the ENGWE EP-2 electric bike in our review.
The electric bike has a massive and sturdy frame, made of aluminum alloy. In addition, the wheels themselves are not spoked, but are made of an aluminum alloy, which gives it a certain stiffness and safety even on rough roads.
Why buy the product?
- It will last you for many years.
- Choose from 3 riding modes: motor only, motor and pedals or pedals only.
- This electric bicycle features a mechanical front and rear disc design that offers control and safety in the grip.
- Thanks to the full front and rear axle of the EP-2 electric bike, you can easily drive on uneven ground with maximum traction.
- LCD night mode and Pedelec hybrid system: with LCD display in night mode for good visibility at night and displays of kilometers and speeds.
- Thick Off-Road Tyres: This mountain bike features 4-inch tyres mounted on 20-inch wheels.
- Lithium battery with large capacity and integrated lock. It is equipped with a smart lithium charger and can be recharged quickly (5 hours).
- Double disc brake and speed control system.
- The integrated lock in the center of the motorized frame locks the battery of the electric bicycle when the bicycle is closed.
- Electric bicycle 48V 12.5A lithium battery supports 25 miles (E-Bike mode).
- The professional 6-speed system offers excellent incline and helps you conquer a variety of terrains.
- This folding electric bike is made of lightweight yet strong aluminum with anti-rust and anti-exposure coating.
- Industrial aluminum alloy frame
5 - MOMA Bikes BIFATG18
Convenient price
Moma is a manufacturer that enjoys the esteem of many cyclists. In her vast catalog there is also room for a good fat bike. We must say that many have been convinced above all by the price of this model. However, the fear of many was that of taking home a poor quality article. Many said they were happily denied. Let me be clear, there are some limits but we will talk about these later.
Let's start with the aluminum frame, which is resistant and absorbs well the stresses typical of off-road routes where it expresses its full potential. The same cannot be said about city routes; there are those who commenting on the purchase have advised against its use in urban contexts mainly because they consider the bicycle too heavy. Very good Shimano TZ-50 21-speed gearbox that is operated comfortably with the lever on the handlebar. The powerful wheels are 26”. Comfortable seating thanks to the professional seat.

Electric Fat Bike: What to Know
As we have anticipated, the Fat eBikes have these particular wheels with much wider tyres than normal. By increasing the surface grip to the ground, they are perfect for tackling mountain routes with difficult terrain. There are also classic MTB Fat models on the market, but never as in this case does the help of pedal assistance become essential. In fact, if such large wheels allow you to better tackle steep or soft ground, on the other hand they make pedaling much more difficult and heavier. Here, then, is that the insertion of a battery and an engine, thus transforming the classic Fat bike into a Fat ebike, becomes essential. The electric support of the pedal assist help riders to better withstand fatigue and to tackle any type of path more easily.
Fat Electric Bikes: The technical Characteristics
Now that we have understood what the wheels with the thickest tyres are for, let's see what are the technical characteristics that an electric fat bike must have.
Generally, as we have often repeated, the electric Fat bike is equipped with these wheels with much wider tyres that generally have these dimensions:
- Rims: 44mm wider
- Tyres: 3.7" wider
However, lately, the widths are increasing more and more and there are also Fat pedal assisted bicycles with 4.8" tyres on the market.
These tyres and these very large wheels serve, as we have already said, to increase the surface that rests on the ground when pedaling, thus being able to move more easily on soft ground and avoiding sinking. Precisely in this regard, the tyre pressure in electric Fat bikes becomes a fundamental characteristic to always keep under control: it must be increased in more compact terrain, such as asphalt and instead decreased in more yielding terrain.
Electric Fat Bikes: motor and battery, what to know
As for the engine, the battery and the entire electrical system of the fat bikes, it is necessary to know that the motors are generally mounted centrally, or to the rear hub. You will hardly find a motor positioned on the front hub because this, especially when tackling climbs on complicated terrain, would make pedaling much more difficult. The motor of a Fat pedal assisted bicycle must then be, as for all other electric bicycles, with a maximum continuous nominal power of 250 watts and the motor must only be activated when you start pedaling.
As for the battery, the average power for a fat tyre eBike must generally be at least 400Wh and, this power is a basic standard, let's say a little also for all mountain bikes.
All Fat electric bikes, but not only, also have a control display on the handlebar that allows you to control all the functions of your Fat Ebike. You can select the level of assistance to the motor and perhaps also check the pedaling sensor which must generally be of effort, in order to allow the motor to follow the requests for greater or lesser power of the biker.
The last technical detail concerning the fat electric bike's control display concerns the fact that the control console must be positioned in an easily accessible place keeping your hands on the handlebars. This is because going to face difficult terrain to manage with your Fat electric bike. it is important to always maintain control of your bicycle.